18 Mar 2014 Update : the plugin has been accepted and is now available on the WordPress.org plugin repo!
Recently, Sucuri posted about 160,000 WordPress sites being used in a DDoS attack. This got me worried about my personal blog, as someone had emailed me last year, claiming that my blog was being used in a DDoS attack. I immediately figured the email was spam and thought “There is no way my site can be so badly compromised!” and I deleted the mail.
The truth was, my personal blog was used in a WordPress Pingback DDoS attack against some poor victim. And I had no idea! My site had unknowingly been used in what I call a “Pingback Botnet”.
And yes, your site could also have been (mis)used.
Get Informed
I first leaned about this type of attack, then WPTavern posted an article about it: How To Prevent WordPress From Participating In Pingback Denial of Service Attacks. They link to the Sucuri blog post and also posted a code snippet that you can paste into your functions.php file to prevent your site from being taken advantage of. It all has to do with the infamous XMLRPC support built into WordPress.
Oh yes, and it is enabled by default as of version 3.5!
Test Yourself
You can test to see if your site was used in the WordPress Pingback Botnet by using Sucuri’s WordPress DDoS scanner. This is what I got back:
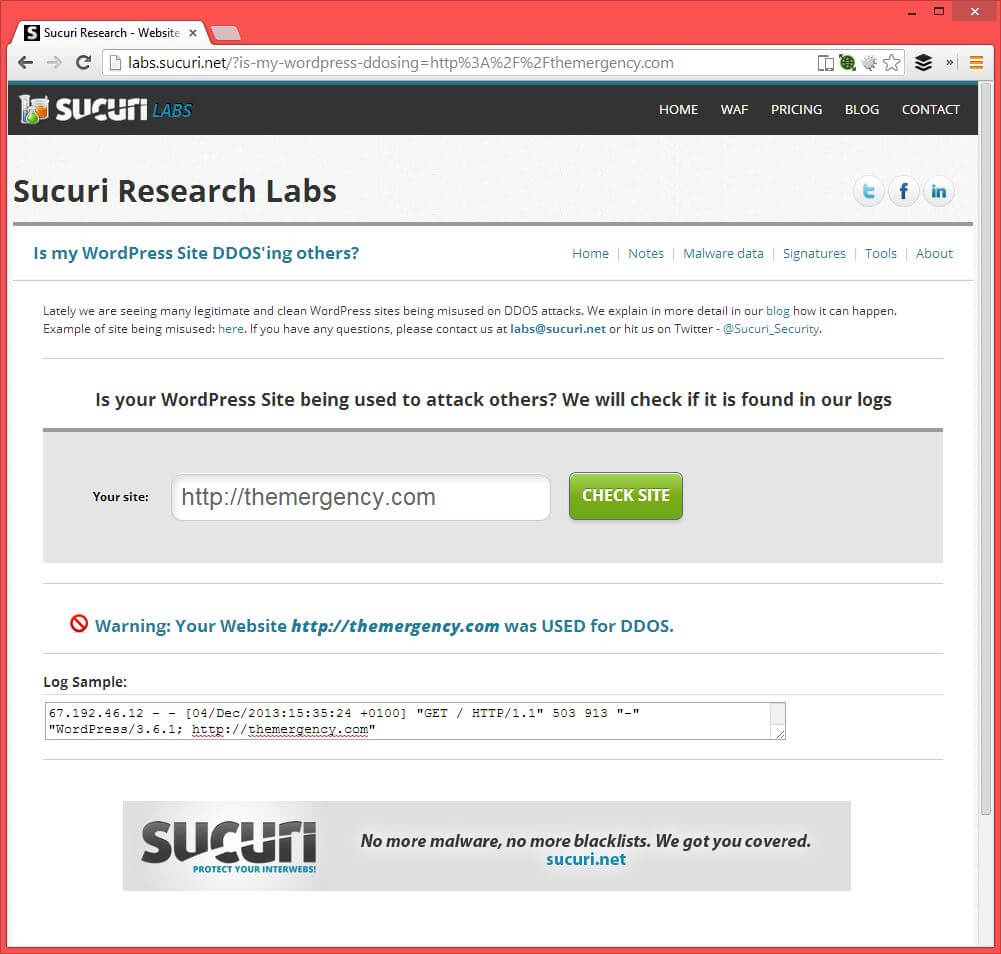
Protect Yourself
Sucuri posted a code snippet which will get you out of the woods:
add_filter( ‘xmlrpc_methods’, function( $methods ) {
unset( $methods['pingback.ping'] );
return $methods;
} );Code language: PHP (php)And then Jeff, over at the Tavern, cleaned it up a bit to make it work with more versions of PHP.
But I was still not happy.
This bit of code is too important to be part of your functions.php file! When you change themes at some point in the future, you can unknowingly open yourself up to become part of the next WordPress Pingback DDoS Botnet.
So I created a simple little plugin with this same code and posted the code on GitHub. It is also available on the WordPress.org plugin repo : Remove XMLRPC Pingback Ping.
Download the zip of the plugin now and activate it.
Test Yourself Again!
If you are paranoid like me, I wanted to make absolutely sure that even after I activated my Remove XMLRPC Pingback plugin, that I was protected. So after a little digging, I managed to figure out how to test my site.
Follow these steps and replace http://YOUR-SITE-URL.com with the URL of your site:
- Install the Chrome extension PostMan
- As your request URL, enter
http://YOUR-SITE-URL.com/xmlrpc.php - Make sure you are doing a
POST - Set your request body to be
RAWwith the following content:
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param><value><string>http://YOUR-SITE-URL.com</string></value></param>
<param><value><string>http://YOUR-SITE-URL.com/hello-world/</string></value></param>
</params>
</methodCall> - Make sure the second param is a valid blog post URL that exists in your WordPress site
- Send the request!
If you get back a response saying the pingback from http://YOUR-SITE-URL.com to http://YOUR-SITE-URL.com/hello-world/ was registered, then your site is wide open. Here is a screenshot from POSTMAN:
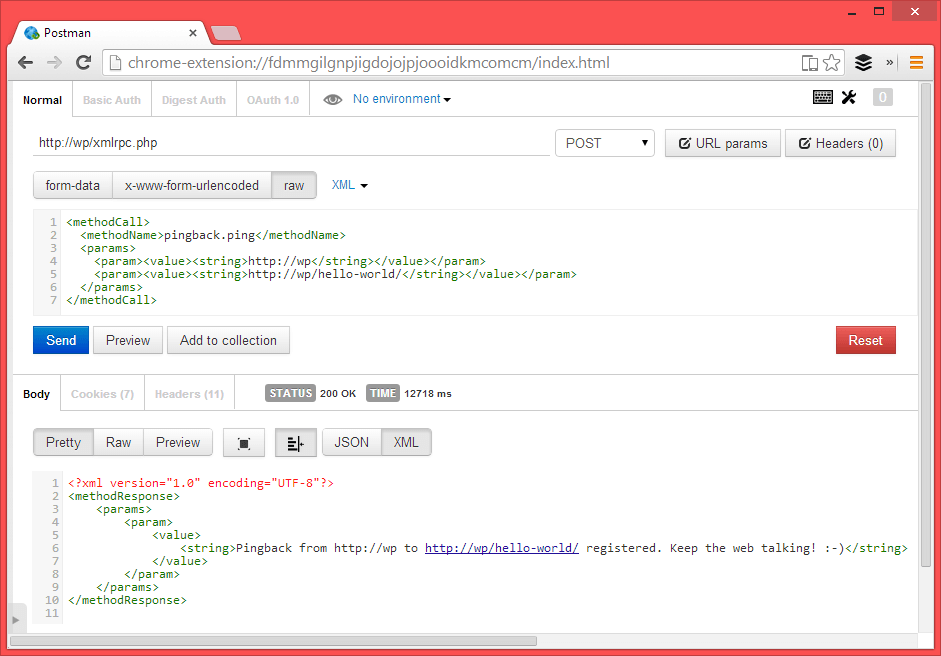
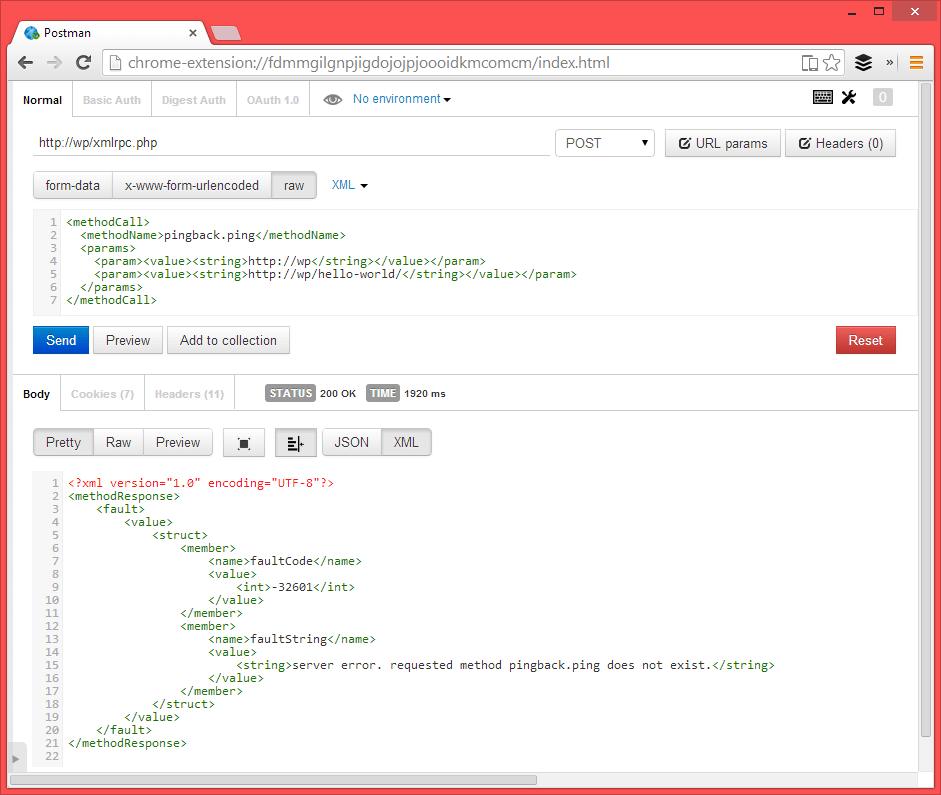
After activating this plugin, sending through the same request as above should result in an error response from the website server error. requested method pingback.ping does not exist., as seen in this screenshot:
In Summary
- Learn more about the threat : Sucuri
- Install the Remove XMLRPC Pingback Ping plugin to protect your site from unknowingly enlisting in the next Pinback Botnet : GitHub repo or WordPress.org repo or Download the zip
Comments are closed.